Tor Browsing. What it is and what it isn't
the only way for near total anonimity

If you are a Pro user, you may be familiar with Tor browsing. Or may be knowing how secure and private it is.
Today, when you pickup your mobile phone or start a computer, there are countless companies and also governments to track on you. Right from your ISP, to Google and Facebook, to NSA and CIA.
May be your state’s government is also spying on you.
The REAL question is - How can you stay completely private without anyone knowing your activity?
You have a lot of things in your computer that those trackers can benefit from. From where to start?
It’s nearly impossible to evade all tracing and stay completely safe.
But Tor browsing is a good tactic that will help you stay somewhat private on the internet. And that works FREE for all.
How Tor works
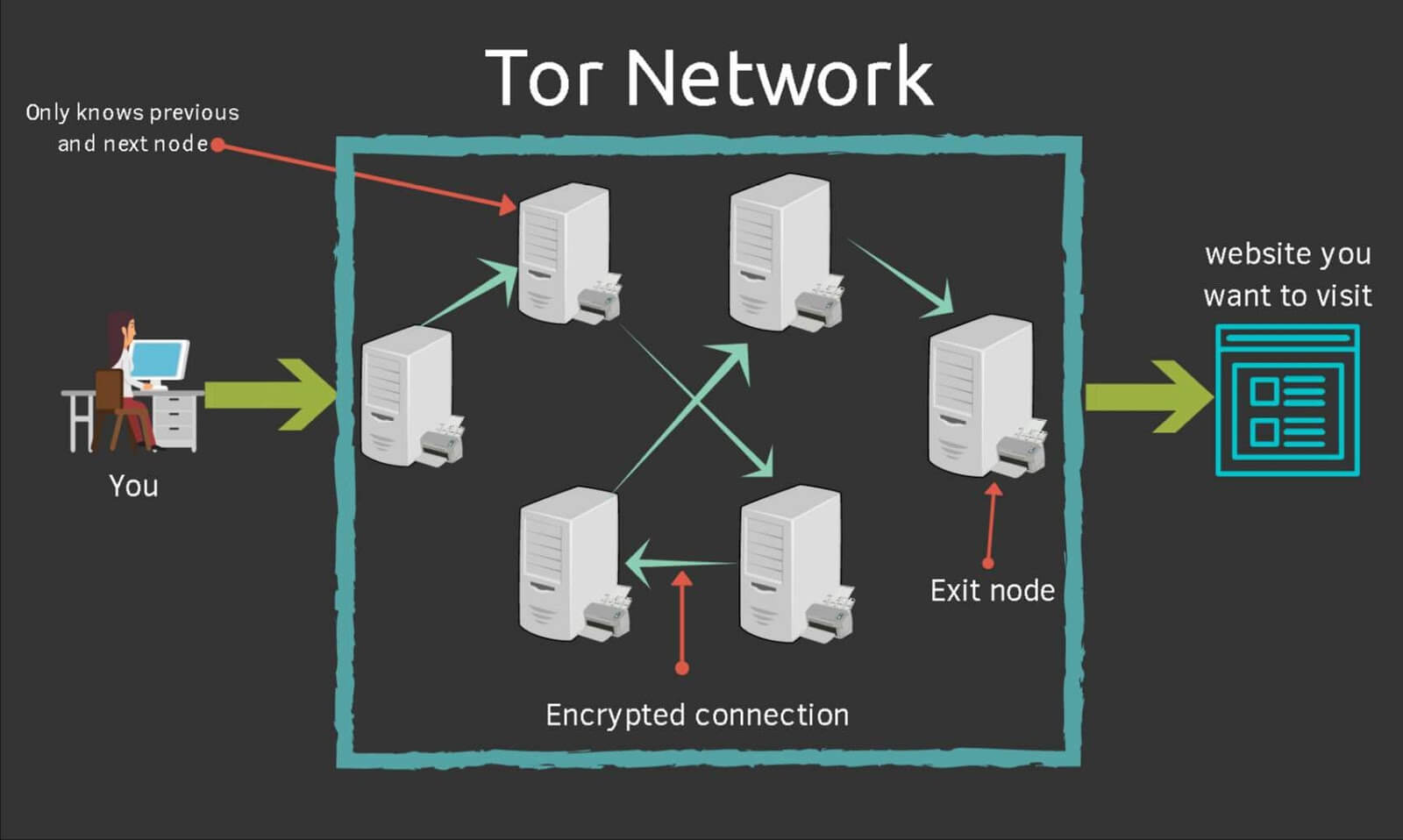
Tor basically hides your personal information such as your device information, IP addresses and websites you visit in encrypted servers.
So instead of you directly connecting to a website, your request to website hops through multiple computers in Tor network.
Tor network is a group of distributed servers around the globe which encrypt your data.
The servers or relays in that path, knows only the previous server from where it received data from and the next server where it will send data to.
And the path changes time to time making it more safe.
So anyone who tries to monitor a relay using traffic analysis cannot tell the destination and source of the data.
Tor only works for TCP streams and not UDP.
But there is are downfalls.
-
The MOST IMPORTANT. The entry and exit node through which your request goes through encrypts and decrypts your traffic. So those relays can know what you are doing. So don’t send any personal information or login to social sites where your identity is revealed
-
You may experience a very slow experience because lot of hops in connection. And you may see content in different language. This is due to the destination website thinking you are actually in that location of that exit node.
-
The data sent over encrypted Tor network has to come out somewhere. The last relay is the Exit node. The exit node just send decrypted data over to the destination. And from there your data is just openly available.
And also exercise caution while accessing or adding personal information through Tor network.
Using Tor Browser
Tor browser is a fork of Mozilla’s Firefox which utilizes Tor network by default.
Your just have to install it as you do with other browser such as Chrome. NO EXTRA STEPS required.
The Tor browser also forces HTTPS for websites so that even the exit node cannot monitor your data and complete connection is secure.
If you want more friendly option, I suggest you for Brave browser which is based on Chromium and uses Tor Window feature.
If you have got enough resources to share, you can start your own relay. That will make already good Tor network even more better
Is Tor Good or Evil
Think of it like a gun which can be used by police for maintining law and order and also by criminals for harming someone. So why not use it for self-defence.
As with any other technology, Tor has some good and bad uses too.
Tor is widely seen to be a tool for common people who want the internet to be democratized from companies, governments, et cetera.
Tor can have legitimate uses. It is used by individuals who are a victim of violence by their oppressive regimes.
It is also used by news organizations such as ‘The Guardian’, ‘The New Yorker’, ‘Pro Publica’, and ‘The Intercept’ to safeguard privacy of whistleblowers.
You can also access websites which are banned in your country or access foreign services.
Tor is also banned in countries such as China and Venezuela because Tor work against some laws of those oppressive regimes.
Do hackers use Tor
May be yes, or may be no.
Just because they have wider and more better options to work with.
The Tor Project FAQ provides a good explanation to that,
Criminals can already do bad things. Since they’re willing to break laws, they already have lots of options available that provide better privacy than Tor provides….
Tor aims to provide protection for ordinary people who want to follow the law. Only criminals have privacy right now, and we need to fix that….
So yes, criminals can in theory use Tor, but they already have better options, and it seems unlikely that taking Tor away from the world will stop them from doing their bad things. At the same time, Tor and other privacy measures can fight identity theft, physical crimes like stalking, and so on.
I believe that Tor is for all who wants to safeguard their privacy.
